Revolutionizing authorization in Laravel applications
We just released the Cerbos Laravel SDK – a seamless way to integrate Cerbos into your Laravel applications. With its objective to demystify the intricate world of roles and permissions, the SDK offers developers enhanced security paired with a polished user experience.
To show its potential, we also built a demo project. Picture a vibrant office where different employees, from varying departments and roles, engage in daily tasks. Within this ecosystem, managing expenses is paramount, and here’s where our cerbos/demo-laravel comes.
The Demo Storyline
We introduce two roles for the purpose of explaining this demo:
Sally: A sales associate operating within the EMEA region.
Derek: Part of the finance department, he holds both user and manager responsibilities.
These roles are pre-configured in the demo to illustrate potential Cerbos implementations for various user types. The demo story is as follows, Sally and Derek (and other pre-populated users of our expense management demo) are attempting various things in the system. In order to provide the needed level of security, Cerbos is used to allow or deny them certain actions, based on their roles in the company, the geography, and other relevant attributes.
Sally, as a sales associate is eligible to create and update her expense entries. Derek, on the other hand, is the finance manager in charge of taking care of expense entries, hence is (apart from viewing them) able to approve or reject them.
Now that we understand the possibilities of the demo, let's go into the setup process.
Deep Dive into Cerbos Policies
Before we jump to the SDK setup part of this walkthrough, let’s peek into the Cerbos configuration for the demo.
Cerbos-related configurations and file structure looks like this:
cerbos > policies >
|-- common_roles.yaml
|-- resource_expense.yaml
|-- resource_features.yaml
`-- config.yamlThe heart and soul of configuration in Cerbos, config.yaml contains the system setup, configurations, and more:
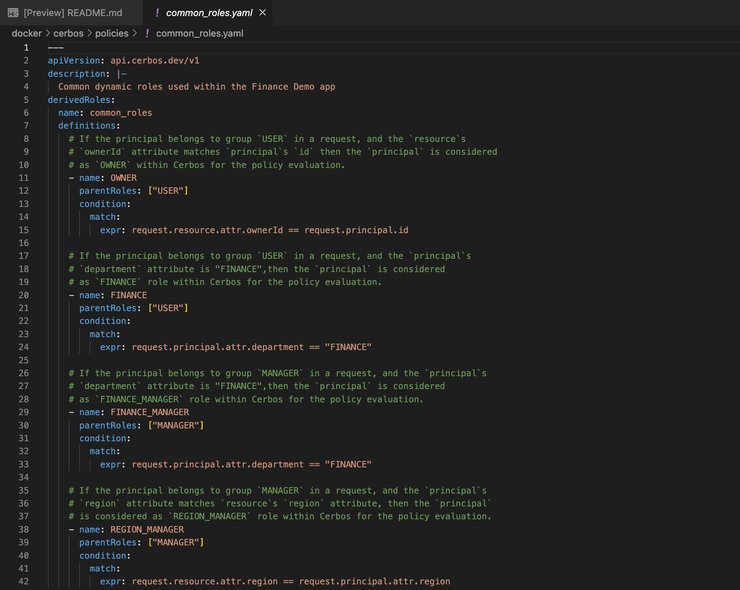
common_roles.yaml provides a guide into the dynamic roles, highlighting conditions that define roles like OWNER, FINANCE, etc:
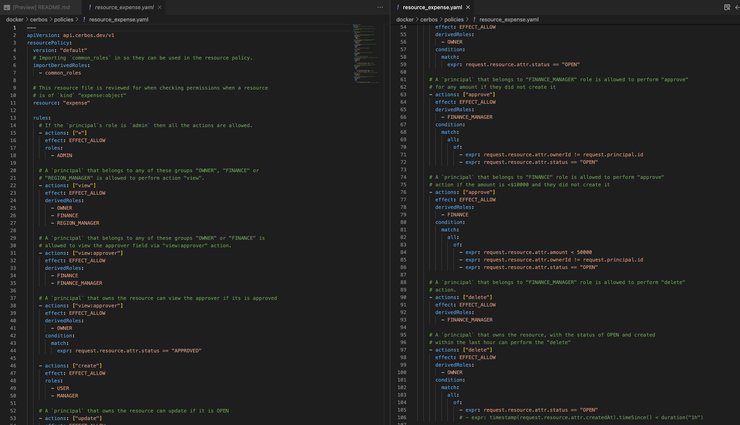
The intricate mapping of roles to the expense resource is held in the resource_expense.yaml. It showcases permissions for actions based on various roles:
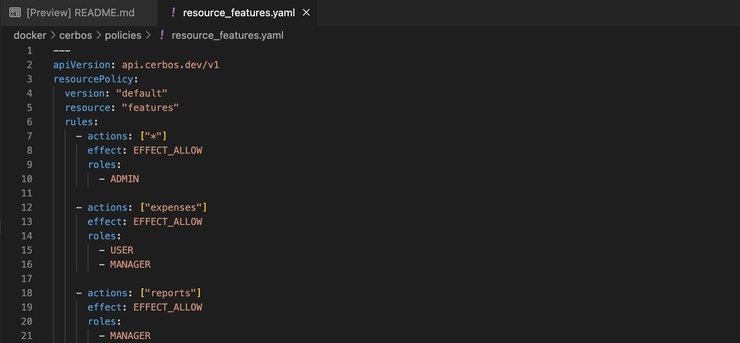
And lastly, we got resource_features.yaml, containing the features resource permissions, distinguishing roles like ADMIN, USER, and MANAGER:
All of the above defines how your application is going to treat various requests made by Sally, Derek and other employees curated for this demo. It gives you a glimpse into how your authorization may look if only you decoupled it from your codebase, and with such ease.
Getting Started with the Cerbos Laravel SDK
Ready to do it yourself? To get started with the Cerbos Laravel SDK, you should install the SDK. One way of doing it can be via Composer by running:
composer require cerbos/cerbos-sdk-laravelService providers are the central place of all Laravel application bootstrapping. As our composer.json defines it properly, the CerbosServiceProvider is auto-discovered and registered by default.
"extra": {
"laravel": {
"providers": [
"Cerbos\\Sdk\\Laravel\\Provider\\CerbosServiceProvider"
]
}
}However, if needed, you can manually register the CerbosServiceProvider by adding it to your config/app.php:
'providers' => ServiceProvider::defaultProviders()->merge([
// ...
\Cerbos\Sdk\Laravel\Provider\CerbosServiceProvider::class,
])->toArray(),Additionally, you can use the artisan vendor command which will create the config/cerbos.php for customizing the Cerbos configuration:
php artisan vendor:publishEach configuration file, such as common_roles.yaml, resource_expense.yaml, and resource_features.yaml, helps in defining specific roles and permissions for different aspects of your application, ensuring that the right people have the right access.
To make the demo more relatable, it comes pre-filled with sample data for users and expenses. These can be found under the seeders:
User Seeds database/seeders/UserSeeder.phpExpense Seeds database/seeders/ExpenseSeeder.php
Running php artisan db:seed seeds the database with the following rows.
Define your own policies in Cerbos and watch as the SDK ensures that API calls adhere to these policies, granting or denying access as appropriate.
Explore & Test: With the sample data seeded, start making API requests. Try registering a new user or approving an expense. See how the SDK evaluates user roles, regions, and departments to make real-time authorization decisions.
In conclusion
The cerbos/demo-laravel project, in conjunction with the Cerbos Laravel SDK, exemplifies how effortless and efficient access control can be. Whether you're building enterprise-grade applications or simple projects, the SDK offers robust, fine-grained authorization checks tailored to your needs.
We invite developers to dive in, explore the demo, and experience first-hand the transformative impact of Cerbos Laravel SDK on their Laravel applications. Created anything fun or useful with it? Join our slack community and tell us all about it.
Book a free Policy Workshop to discuss your requirements and get your first policy written by the Cerbos team
Related Articles
Subscribe to our newsletter
Join thousands of developers | Features and updates | 1x per month | No spam, just goodies.